Are "CAPTCHA" losing their value for security? New bypass method completely avoids the problem of reading them.
By Andrew Pollack on 01/11/2008 at 01:01 PM ESTYou might be a hacker.
If you've ever been asked to read an image of distorted letters and numbers, then type them into a field on a web form, you're using a Captcha.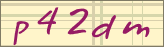 The thing is, even though the programs that make the images are keeping ahead of the programs that read them, it is quickly loosing its effectiveness. Hackers are now using YOU to do the work.
The thing is, even though the programs that make the images are keeping ahead of the programs that read them, it is quickly loosing its effectiveness. Hackers are now using YOU to do the work.
Suppose a comment spammer wants to automate adding stuff to your blog, but you've got captcha codes set up. These spammers are resourceful people. Here's a method I heard about the other day.
1. Identify the part of the target page that shows the captcha image.
2. Code a script to read the page, and grab that image location - maybe even copy down the image.
3. Set up a PORN, Free Music, or other such site that also uses captcha for access. However, instead of having your own captch generator program, each time someone loads a page that asks for a user to interpret and enter the captcha digits, serve them the image from the page you're targeting.
4. The user, to get access to your porn or music site dutifully interprets the captcha image you shown him, and types it in. He submits the page, and now you have your human interpreted captcha result to use against your target page.
This method can easily and quickly be set up so that every single time you get some user to go through YOUR page using captcha, you're also using that same person to give you the data you need to create another bogus yahoo mail account, post a bogus blog comment, or otherwise mess with people.
Brilliant. Evil, but brilliant. Its a little insight into how the mind of a hacker works.
standard attack strategy these days.
As always it's an arms race.
against high-profile blogs -- of course, high-profile blogs need to be using
some sort of moderation or URL-checking, anyway.
there's never going to be enough people filling out these fake captcha forms
for spammers to ever be much of a problem. There's always going to be more
blogs than people cracking them, and for this to work, it needs to be the other
way around.
The hacker sets up a porn site, or an unsubscribe on a spam list, or something
like that. Users doing what users do, see the captcha as part of their normal
process. They never know it came from somewhere else.
Other Recent Stories...
- 01/26/2023Better Running VirtualBox or VMWARE Virtual Machines on Windows 10+ Forgive me, Reader, for I have sinned. I has been nearly 3 years since my last blog entry. The truth is, I haven't had much to say that was worthy of more than a basic social media post -- until today. For my current work, I was assigned a new laptop. It's a real powerhouse machine with 14 processor cores and 64 gigs of ram. It should be perfect for running my development environment in a virtual machine, but it wasn't. VirtualBox was barely starting, and no matter how many features I turned off, it could ......
- 04/04/2020How many Ventilators for the price of those tanks the Pentagon didn't even want?This goes WAY beyond Trump or Obama. This is decades of poor planning and poor use of funds. Certainly it should have been addressed in the Trump, Obama, Bush, Clinton, Bush, and Reagan administrations -- all of which were well aware of the implications of a pandemic. I want a military prepared to help us, not just hurt other people. As an American I expect that with the ridiculous funding of our military might, we are prepared for damn near everything. Not just killing people and breaking things, but ......
- 01/28/2020Copyright Troll WarningThere's a copyright troll firm that has automated reverse-image searches and goes around looking for any posted images that they can make a quick copyright claim on. This is not quite a scam because it's technically legal, but it's run very much like a scam. This company works with a few "clients" that have vast repositories of copyrighted images. The trolls do a reverse web search on those images looking for hits. When they find one on a site that looks like someone they can scare, they work it like ......
- 03/26/2019Undestanding how OAUTH scopes will bring the concept of APPS to your Domino server
- 02/05/2019Toro Yard Equipment - Not really a premium brand as far as I am concerned
- 10/08/2018Will you be at the NYC Launch Event for HCL Domino v10 -- Find me!
- 09/04/2018With two big projects on hold, I suddenly find myself very available for new short and long term projects.
- 07/13/2018Who is HCL and why is it a good thing that they are now the ones behind Notes and Domino?
- 03/21/2018Domino Apps on IOS is a Game Changer. Quit holding back.
- 02/15/2018Andrew’s Proposed Gun Laws


Also, there's a good posting over on the "Coding Horror" web site about how
even a very simple captcha works great for most web sites.
High-value targets (like ticketmaster) do need to be thinking about this issue.